Change PostgreSQL Password Authentication to SCRAM-SHA-256
By default (out-of-the-box installation), Postgres uses md5 encryption. Beginning with Postgres 10, you can change your PostgreSQL password authentication to SCRAM-SHA-256, which is a more secure authentication method than md5 and plain password.
Following are steps to change your local PostgreSQL password authentication to SCRAM-SHA-256.
-
Download and install a PostgreSQL management tool or you can use the tool that is embedded in your instance of IDE, pgAdmin, DBeaver, and so on.
-
Connect the tool to your current database.
-
Run the following query. This query displays your current password encryption method, such as md5.
CopySHOW password_encryption;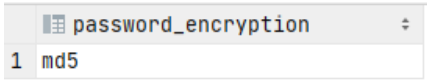
-
Run the following query. This query displays your current hashed password.
CopySELECT rolpassword from pg_authid where rolname = '{your-db-user-name}';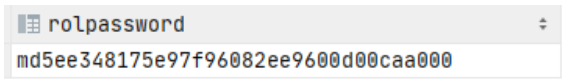
-
Run the following query. This query changes your current hashing method from md5 to SCRAM-SHA_256.
CopySET password_encryption = 'scram-sha-256'; -
Run the following query. This query changes your current password to use the SCRAM-SHA-256 password encryption.
CopyALTER USER "{your-db-user-name}" with password '{your-new-db-password}'; -
Run the following query again. The query now displays your password in SCRAM-SHA-256 format.
CopySELECT rolpassword from pg_authid where rolname = '{your-db-user-name}';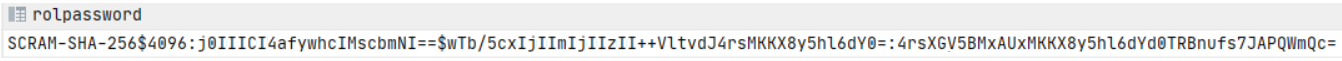
-
Open the PostgreSQL.conf file. Then change the password_encryption to scram-sha-256.
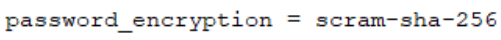
-
(Optional) Open the pg_hba.conf file. Then change the method to scram-sha-256.
If md5 is specified as a method in the pg_hba.conf file but your password on the server is encrypted for SCRAM-SHA-256, then SCRAM-based authentication will automatically be used instead, in an effort to ease transition from the md5 method to the SCRAM method. For more information, refer to the PostgreSQL documentation.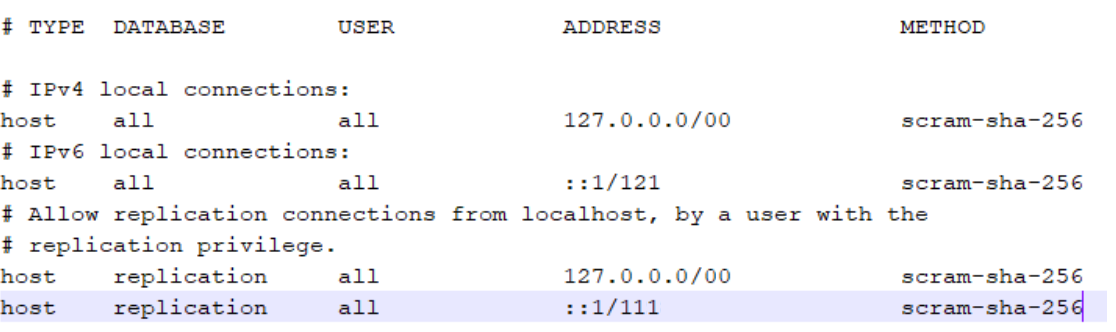
-
Restart the PostgreSQL service.
-
Run the following query again. The result should display a password encryption method of scram-sha-256.
CopySHOW password_encryption;