Configure OAuth 2.0 authentication
You can configure authentication via OAuth 2.0 in the API Engine to communicate with your webservices.
To do so, follow the steps below:
-
Select your API Module.
-
In the Technical View, click on the Auth tab.
-
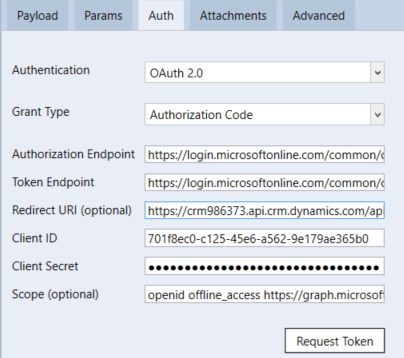
In the Authentication drop-down menu, select OAuth 2.0.
-
Select your grant type from the Grant Type drop-down menu. This specifies how the application receives the access token.
-
Depending on your grant type, enter the following specifications:
-
Authorization Endpoint: enter the authorization server URI.
-
Token Endpoint: enter the token server URI.
-
Redirect URI: optionally, enter the redirect URI.
-
Code Challenge Method: select the method to transform the code verifier into the code challenge from the Code Challenge Method drop-down menu. You can choose SHA-256 algorithm or Plain text to generate the code challenge. Select Plain when the code challenge is the same as the code verifier.
-
Code Verifier: optionally, enter a character string to connect the authorization request to the token request. This is a cryptographically random string using the characters A-Z, a-z, 0-9, and the punctuation characters -._~ (hyphen, period, underscore, and tilde), between 43 and 128 characters long. If you leave this field empty, the value that has 43 characters is automatically generated after you click Request Token.
-
Client ID: enter the client identifier, that is the application's registration information issued by the authorization server.
-
Client Secret: enter the client secret, that is the password to authenticate the identity of the application.
-
Scope: optionally, indicate which scope of permissions the application requests. Enter one or more space-separated strings, e.g. openid.
-
Username: enter your user name.
-
Password: enter your password.
-
Configure OAuth 2.0 authentication
If you selected grant types Authorization Code or Authorization Code (With PKCE), a browser window opens in which you have to authorize access to your account.
For all other grant types, your access token is issued immediately.

|
If you use Microsoft Azure AD Connect as your authentication service, API Scan stores returned cookies in the Cookies window. This allows the system to use the cookies for authorization in the next call. |
Request a new access token if token has expired
Access tokens expire after a certain period of time and become invalid. This means that a new access token must be requested, which might affect your API TestCases. In the following cases, the API Engine automatically requests a new valid access token to continue your API TestCases:
-
If an access token expires and there is a refresh token. The API Engine uses the refresh token to request a new access token.
-
If the access token expires and there is no refresh token. The API Engine requests a new access token if you use the grant type Password or Client Credentials.
In case there is no refresh token and you use the grant type Authorization Code, Authorization Code (With PKCE), or Implicit, you have to request a new token manually (see step 3) to continue your TestCase.